
Craig Lusher from our Secure team provides a comprehensive analysis of the latest Distributed Denial of Service (DDoS) statistics from the first quarter of the year and their implications for cybersecurity trends.
The first quarter of 2025 has revealed significant changes in the DDoS threat landscape, characterised by a substantial increase in attack frequency, the emergence of ‘carpet bombing’ techniques and growing trends targeting the iGaming sector. With attack methodologies evolving and becoming more sophisticated, this report provides critical insights for cybersecurity planning and threat mitigation.
The first quarter of 2025 has shown a noticeable increase in DDoS attack activity, with 161 attacks recorded. This represents a rise from 4Q 2024’s 138 attacks and a dramatic increase from 1Q 2024’s 58 attacks. The most active month was February, which continues to show vulnerability during winter months.
1Q 2025 showed the following patterns in attack intensity:
While individual attack sizes appear smaller compared to historical peaks (2Q 2023’s 560.6 Gbps), this represents a strategic shift rather than reduced threat capability. Intelligence indicates that attackers now possess capabilities exceeding 500 Gbps but are employing more targeted and distributed approaches that can bypass traditional detection mechanisms.
1Q 2025 has shown a marked increase in attacks specifically targeting the online gambling and casino sector, with intelligence indicating a 400% rise in attacks against these entities since February. This industry-specific targeting represents a prominent trend that requires specialised attention and defence mechanisms.
Key statistics for 1Q 2025:
On 26 February, a carpet-bombing incident targeted 53 networks within a short 6-minute window (03:41-03:47 UTC). While this attack peaked at 150 Gbps with 120 Mpps, its distributed nature allows it to circumvent traditional defence systems, potentially resulting in a significant customer impact.
Comparing 1Q 2025 with recent quarters reveals several trends:
This shows a clear trend of increasing attack volumes over the past three quarters, with a 372% increase from 3Q 2024 to 1Q 2025.
While individual attack volume metrics appear to show decreasing intensity, this is misleading as attacks are now distributed across multiple targets simultaneously, making traditional detection mechanisms less effective.
The number of affected customers has increased dramatically in 1Q 2025, indicating a broader targeting strategy. Of particular note is the observed ‘spray’ technique that targets entire network Classless Inter-Domain Routing (CIDR) blocks rather than individual IPs, affecting multiple customers simultaneously.
1Q 2025 has seen the emergence of carpet bombing or spray attacks that distribute traffic across multiple hosts within targeted IP ranges. These attacks:
Comparing 1Q 2025 to 1Q 2024 shows significant changes in the threat landscape:
Intelligence indicates a notable correlation between DDoS attacks and subsequent data breaches in the iGaming sector. 1Q 2025 has seen examples of multiple organisations experiencing what appears to be a new attack pattern:
Unlike traditional ransomware operations, these attacks show no ransom demands prior to data release, indicating a potential shift in threat actor motivations from financial gain to maximum disruption or competitive advantage.
The transition to carpet-bombing techniques represents a significant evolution in DDoS tactics. These attacks distribute traffic across multiple targets within a network range, using traffic volumes per target that stay below conventional detection thresholds.
Intelligence indicates a targeted campaign against the iGaming sector, with a 400% increase in attacks since February 2025.
The average attack duration has increased dramatically to 4.3 hours, with the longest attack lasting 54 hours. Short, intense attacks (3-6 minutes) are now frequently observed as reconnaissance to test defence capabilities before launching larger campaigns.
Intelligence suggests a rising trend of AI technology adoption by threat actors. Self-hosted AI tools are enabling more sophisticated and unpredictable attack patterns that traditional defence mechanisms struggle to detect. These AI-enhanced attacks show several characteristics:
Based on 1Q 2025 attack patterns, particularly the emergence of carpet-bombing techniques, the following defence strategies are recommended:
The increase in attack volumes and sophistication in 1Q 2025 indicates a significant evolution in the threat landscape. Organisations should prepare for:
The 26 February incident, which affected 53 networks within a 6-minute window, demonstrates the effectiveness of these new attack methodologies and highlights the need for enhanced detection and mitigation capabilities.
Our best-in-class DDoS solution continues to evolve and in recent months we have amplified our scrubbing capacity to 5+ Tbps, as well as increased our scrubbing centres geographically deployed across multiple continents. Locations include Los Angeles, Chicago, New York, Miami, London, Amsterdam, Frankfurt, Singapore, Hong Kong and Sao Paulo.
Key features of our mitigation solution:

DDoS protection should also form part of a wider, multi-layered approach to cybersecurity. A 360-degree, end-to-end protection strategy should include DDoS mitigation solution as well as WAF/WAAP protection, MDR/EDR services, SIEM and SOC resources, VAPT assessments, backup solutions, and mobile device, phishing defence and MFA services.
This is the only way to have multiple protections in place for each attack type and to ensure the greatest level of resilience.
To learn more about how Continent 8 can help protect your organisation, contact a member of the team via sales@continent8.com or our Contact Us form.
Craig Lusher from our Secure team provides a comprehensive analysis of the latest Distributed Denial of Service (DDoS) statistics from the fourth quarter of the year and their implications for cybersecurity trends.
The fourth quarter of 2024 marked a significant shift in DDoS attack patterns, with 138 recorded incidents. This represents a substantial increase from 3Q’s 37 attacks, though remaining well below historical peaks like 2Q 2023’s 1,106 attacks. October emerged as the most active month, aligning with historical patterns of increased 4Q activity.
This is a trend not just at Continent 8. In fact, 4Q also happened to see the largest DDoS attack ever recorded, with Cloudflare mitigating a 5.6 (Terabits per second) Tbps Mirai-variant botnet attack on one of their customers on October 29.
4Q 2024 demonstrated interesting patterns in attack intensity:
This quarter’s largest attack of 13.4 Gbps represents a decrease from 3Q 2024’s peak of 37.0 Gbps. For perspective, this is dramatically lower than 4Q 2023’s peak of 412.9 Gbps, indicating a significant shift in attack methodologies.
Key statistics for 4Q 2024:
Key statistics for 4Q 2024:
Comparing 4Q 2024 with recent quarters reveals several interesting trends:
This shows a significant escalation in attack frequency during 4Q.
While attack frequency increased, intensity continued to decrease throughout the year.
The decrease in affected customers coupled with the dramatic increase in attacks per customer suggests a shift toward more targeted campaigns.
Comparing 4Q 2024 to 4Q 2023 shows significant changes in the threat landscape:
The higher volume but lower intensity of attacks suggests a fundamental shift in attacker strategies, focusing on persistent, lower-threshold campaigns rather than high-impact events.
The concentration of attacks on fewer customers, with more attacks per target, indicates a move toward more sophisticated, focused operations.
The shorter average attack duration (17.6 minutes) combined with increased frequency suggests a tactical shift toward ‘pulse’ style attacks rather than sustained campaigns.
While individual attack intensities have decreased significantly year-over-year, the dramatic increase in frequency and focus on specific targets suggests an evolution in threat actors’ strategies. The pattern of increased 4Q activity appears to be holding true, though manifesting differently than in previous years.
Organisations should prepare for:
Our best-in-class DDoS solution continues to evolve and in recent months we have amplified our scrubbing capacity to 5+ Tbps, as well as increased our scrubbing centres geographically deployed across multiple continents. Locations include Los Angeles, Chicago, New York, Miami, London, Amsterdam, Frankfurt, Singapore, Hong Kong and Sao Paulo.
Key features of our mitigation solution:

DDoS protection should also form part of a wider, multi-layered approach to cybersecurity. A 360-degree, end-to-end protection strategy should include DDoS mitigation solution as well as WAF/WAAP protection, MDR/EDR services, SIEM and SOC resources, VAPT assessments, backup solutions, and mobile device, phishing defence and MFA services.
This is the only way to have multiple protections in place for each attack type and to ensure the greatest level of resilience.
To learn more about how Continent 8 can help protect your organisation, contact a member of the team via sales@continent8.com or our Contact Us form.
A Distributed Denial-of-Service (DDoS) attack, whether large or small, can cause significant downtime and financial loss.
But what exactly is a DDoS attack?

In this blog, Craig Lusher, Product Principal of Secure Solutions at Continent 8 Technologies, will explore what a DDoS attack is, the different types of DDoS attacks, and the best practices for mitigating DDoS attacks.
A DDoS attack is like an unexpected traffic jam on an otherwise free-flowing highway. The attacks attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming it with a flood of Internet traffic.
DDoS attacks leverage multiple compromised computer systems as sources of attack traffic, including computers and Internet of Things (IoT) devices. They involve networks of Internet-connected devices infected with malware, controlled remotely by attackers and forming a botnet.
The process begins with the attacker creating the botnet by infecting multiple devices. Next, they send remote commands to the botnet, which then sends numerous requests to the target’s IP address. This flood of requests overwhelms the server or network, resulting in a denial-of-service for legitimate traffic.
Several high-profile DDoS attacks have made headlines in recent months, showcasing the damage these attacks can inflict, regardless of industry.
DDoS attacks come in various forms. DDoS attacks can be categorised into three main types based on which part of the network connection they target.
A volumetric attack aims to overwhelm the bandwidth between the target and the Internet with massive amounts of data. The attack often uses amplification techniques to ensure it consumes all available bandwidth.
A good example is Domain Name System (DNS) amplification. This method is done through a small query to an open DNS server with a spoofed IP address, resulting in a large response being sent to the victim, ultimately overwhelming their bandwidth.
A protocol attack exploits weaknesses in network protocols, particularly layers 3 and 4 of the protocol stack. It disrupts service by consuming server resources or network equipment resources like firewalls and load balancers.
SYN flood is a popular method. It overwhelms the target by sending many TCP SYN packets with spoofed IP addresses, exhausting resources by never completing the TCP handshake.
The application layer attack targets the application itself, often appearing as legitimate traffic. It exhausts the target’s resources and creates a denial-of-service. The attack preys on the application layer (Layer 7 of the OSI model) where web pages are generated and delivered in response to HTTP requests.
HTTP flood method, for example, generates multiple HTTP requests to flood the server. These requests overwhelm the server and cause a denial-of-service. These can range from simple attacks with one URL and similar IP addresses to complex attacks using many IP addresses and random URLs.
The main challenge in mitigating a DDoS attack is distinguishing between legitimate traffic and attack traffic. For example, a legitimate surge from a product release differs from an attack surge from known attackers.
These attacks are also multi-vector. This means they use multiple pathways to overwhelm targets, making it harder to distinguish between attack and normal traffic. A layered approach, such as combining DNS amplification (targeting layers 3/4) with an HTTP flood (layer 7), requires varied strategies for mitigation.
Due to these complexities, protecting a site from DDoS attacks requires a multi-layered approach. In the event of unforeseen circumstances, having a clear plan in place for responding to DDoS attacks can minimise downtime and damage.
Finding a service specialising in DDoS solutions can be a great help, but there are layers to the mitigation process.
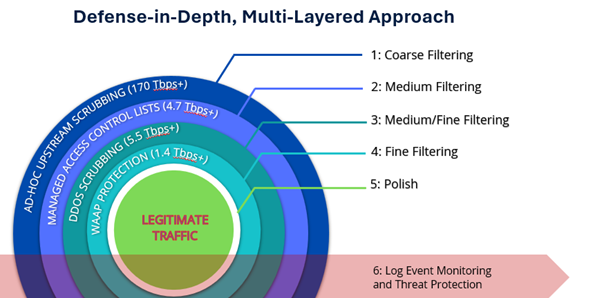
At Continent 8, we advocate for a ‘defence-in-depth’ strategy, where multiple layers of security controls are implemented throughout the organisation’s IT environment. This ensures that if one layer is breached, additional layers are in place to prevent or mitigate the attack.
Continent 8’s defence-in-depth, multi-layered approach includes:
Continent 8 offers the most comprehensive cybersecurity solutions equipped to meet today’s emerging DDoS threats.
Continent 8 provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your organisation’s digital assets in the face of evolving cyber threats. For more information on how Continent 8 can support your cybersecurity initiatives, email sales@continent8.com or fill out our Contact Us page.
Craig Lusher from our Secure team takes a deep dive into the latest DDoS stats from the second quarter of the year
As was the case in the first quarter of 2024, Continent 8 continues to see a decline in DDoS attacks against its customers with just 32 incidents reported across customers in the second quarter of the year. This marks a 45% decrease from the 58 attacks recorded in the previous quarter and is a mere fraction of the 1,106 DDoS attacks successfully thwarted during the corresponding period in 2023.
The quarter’s fluctuation in the number of attacks per month, with 8 in April, 5 in May and 19 in June, indicates varying attack campaigns or possibly enhanced defensive strategies.
The intensity of attacks in the second quarter of 2024 escalated significantly than in the previous quarter in terms of peak attack size:
This quarter’s surge in peak attack intensity, particularly in June, indicates a concerning trend towards more powerful DDoS attempts, despite their decreased frequency.
The highest number of attacks a single customer faced was 7, a significant reduction from the peak of 25 attacks in the first quarter. This data indicates a shift towards a more distributed pattern of attacks in the second quarter compared to the first quarter.
The timing and frequency of attacks in the second quarter of 2024 reveal some interesting trends:
These figures indicate that while there were fewer attacks overall, they tended to last longer on average, with some attacks being significantly more persistent than in the previous quarter. Prolonged attacks can strain resources for unprotected customers, potentially leading to substantial disruptions if critical systems or services are compromised by malicious activity.
The second quarter of 2024 witnessed a significant reduction in overall DDoS activity compared to the first quarter. However, there has been a concerning uptick in the intensity of attacks, particularly in June, posing a greater risk of potential damage. The fluctuations observed throughout the quarter, peaking with a spike in June, suggest evolving DDoS attack strategies. Employing an advanced DDoS mitigation system and solution is essential to safeguard against potential threats.
Our best-in-class DDoS solution continues to evolve and in recent months we have amplified our scrubbing capacity to 2.5+ Tbps, as well as increased our scrubbing centres geographically deployed across multiple continents. Locations include Los Angeles, Chicago, New York, Miami, London, Amsterdam, Frankfurt, Singapore, Hong Kong and Sao Paulo.
Key features of our mitigation solution:

DDoS protection should also form part of a wider, multi-layered approach to cybersecurity. A 360-degree, end-to-end protection strategy should include DDoS mitigation solution as well as WAF/WAAP protection, MDR/EDR services, SIEM and SOC resources, VAPT assessments, backup solutions, and mobile device and phishing defence services.
This is the only way to have multiple protections in place for each attack type and to ensure the greatest level of resilience.
To learn more about how Continent 8 can help protect your organisation, contact a member of the team via sales@continent8.com or our Contact Us form.
Anc News TV artigo sobre o continente 8 e parceria IPC nas Filipinas.
Global data centre and managed service provider Continent 8 Technologies has announced key partnerships to enable the delivery of its globally respected services directly to businesses throughout the Philippines. The new partners approached Continent 8 as they wished to offer the company’s advanced DDoS (Distributed Denial of Service) protection and mitigation services alongside Continent 8’s global private connectivity to Philippines based companies.
In 2016, Continent 8 announced the completion of its latest network expansion, bringing its European, North American and Asia Pacific networks together to give true global coverage across a multi-terabit network. Now with over 25 points of presence globally, this enables the company to deliver its world-class service portfolio into a number of additional regions.
Partnerships have been announced with IP Converge Data Services Ltd (IPC, an ePDLT company) and LR Data Center and Solutions, Inc, both headquartered in Makati City, Manila. These significant players in the local connectivity and data centre markets were carefully selected by Continent 8 as they are both businesses which share Continent 8’s values of service excellence, innovation and integrity.
By forging these strategic partnerships, Continent 8 brings proven expertise and the delivery, management and support is carried out by the partners – enabling continuity, use of local knowledge and leveraging existing relationships. This model is now to be extended to other regions in the coming months through more carefully selected partners who share Continent 8’s ethos for service excellence and who wish to bring Continent 8’s service portfolio to their own customer base.
Michael Tobin, Co-founder and Chief Executive Officer commented “With nearly 20 years of experience and operations, we have built a global reputation for service excellence alongside a unique global footprint of data centres and network points of presence. By partnering with IPC and LR Data, we bring to the table advanced DDoS Mitigation services to Philippine enterprises, at a time when attacks are becoming increasingly prolific,”
Further services will be rolled out in due course and will allow Filipino businesses to connect globally using their local, trusted partners.